03. First Update - 9:00am Monday
First Update - 9:00am Monday

You’ve received the following details in a brief.
- Hospital A, Hospital B, and Hospital C each noticed that when trying to log into their centralized log management systems, the following message pops up.
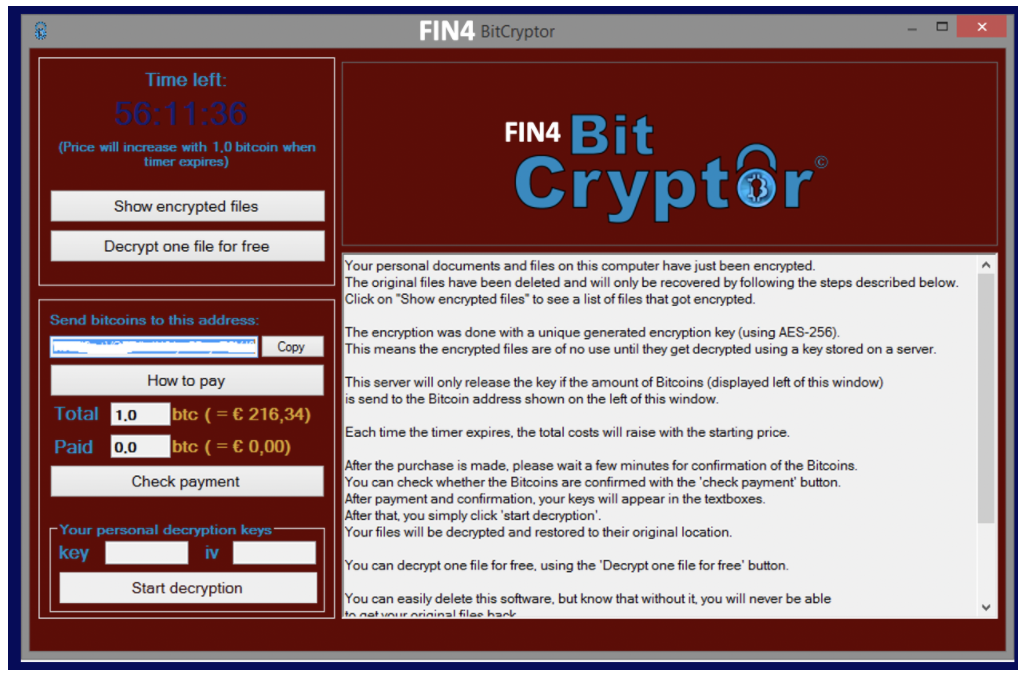
- The hospitals have disclosed that each incident started with a user in the technology department opening an email attachment resource. This activity has not yet been seen in Hospital X.
Action: Conduct research to understand what type of threat could be involved, who is the threat actor behind the threat, and how they are motivated, and what attack tactics they are using or might use in the future. Add a threat profile to the report template.